Nmap Tool For Mac
It was designed to rapidly scan large networks, but works fine against single hosts. Nmap runs on all major computer operating systems, and official binary packages are available for Linux, Windows, and Mac OS X. Nmap, the network mapping tool, is the starting point when analysing any network. It is an exciting tool — compact and power-packed. This article looks at the range of functions and options it supports.
Ever wondered how assailants know what slots are open up on a program? Or how to find out what solutions a computer is operating without simply requesting the web site admin? You can do all this and more with a convenient little tool known as Nmap. What is definitely Nmap? Short for 'network mapper,' nmap is usually a veritable toolshed of efficiency to carry out network scans.
It can become used for security scans, basically to determine what providers a web host is running, to 'finger-print' the operating system and programs on a sponsor, the kind of firewall a sponsor is making use of, or to perform a quick stock of a nearby network. It is definitely, in brief, a really good tool to know.
It'beds famous, as well. As soon as you get to understand Nmap a bit, you'll notice that it makes all forms of in films. In this tutorial, I'll cover some of the basics of making use of Nmap and provide some good examples you can use quickly. Obtaining Nmap and Fundamental Use You'll discover Nmap packaged for many main Linux distros. The almost all recent discharge of Nmap emerged out in early 2010, so the almost all recent version (5.21) might not end up being in the current stable releases. You can find the sources and some binariés on the. Thé fundamental format for Nmap is usually Nmap Check Type Options target.
Let's say you desire to check out a sponsor to see what operating system it is certainly operating. To do this, run the using: nmap -U target.web host.com Take note that Nmap requires root privileges to run this type of check. The check out might take a minute or so to run, so become individual.
When it finishes, you'll discover something like this: Beginning Nmap 5.21 ( ) at 2010-02-27 23:52 EST Nmap scan statement for 10.0.0.1 Sponsor is up (0.0015s latency). Not proven: 997 closed ports PORT STATE SERVICE 53/tcp open domain name 5009/tcp open up airport-admin 10000/tcp open snet-sensor-mgmt Macintosh Address: 00:11:24:6B:43:E2 (Apple company Pc) Gadget kind: WAP printer Jogging: Apple embedded, Canon embedded, Kyocera inserted, Xerox inlayed OS information: VxWorks: Apple AirPort Intensive v5.7 or Airport terminal Show v6.3; Canon imageRUNNER printer (5055, C3045, Chemical3380, or Chemical5185); Kyocera FS-4020DIn printing device; or Xerox Phasér 8860MFP printing device Network Range: 1 hop OS detection performed. Please report any wrong outcomes at.
Nmap performed: 1 IP address (1 web host up) scanned in 10.21 seconds As you can see, Nmap provides a great deal of data. Right here it will take a guess at the operating system that might be running on the system. I ran this particular scan against an Apple company Airport Great router. As an added reward, Nmap informs me that the gadget is certainly one jump away, the Mac pc tackle of the device and manufacturer of the NIC, the open up ports, and how long the scan took.
Right here's the outcome of another check, against a desktop computer machine operating Ubuntu 9.10: Beginning Nmap 5.21 ( ) at 2010-02-28 00:00 EST Nmap scan statement for 10.0.0.6 Sponsor can be up (0.0039s latency). Not really demonstrated: 999 shut ports Interface STATE Provider 22/tcp open ssh Macintosh Deal with: 00:17:08:2A:D6:F0 (Hewlett Packard) Device kind: common purpose Jogging: Linux 2.6.X OS information: Linux 2.6.19 - 2.6.31 Network Distance: 1 jump OS detection performed. Make sure you document any wrong results at.
Nmap done: 1 IP address (1 host up) scanned in 3.40 secs Here we observe that the system provides an HP NlC (it's án HP workstation), running the Linux kernel somewhere between Linux 2.6.19 and 2.6.31. You may not really be able to get an precise recognition of the operating system down to the edition of Linux. Exercise Offers In the examples above, I opted a nearby router and oné of my workstations in part because I have got the authorization to check out them. You can make use of Nmap to check out virtually any host. Nevertheless, it's a poor idea to operate many scans against offers you're not in control of or don't possess permission to scan. The Nmap people have a check web host at scanme.nmáp.org that cán be used for screening, so lengthy as you're also not operating any exams of uses or Denial of Services (DoS) attacks. Some admins put on't appreciate unpredicted scans, so use best common sense and restrict scans to hosts that are on your own system or that you have got permission to check.
It may furthermore be against your ISP'beds terms of support to use some of Nmap'h more intense scan features, so become cautious out there! Multiple Owners You can check out more than one web host at a period using nmap. If you're also making use of IP contact information, you can state a range like 10.0.0.1-6 or a range like 10.0.0.0/24. The 10.0.0.1-6 would check out offers 10.0.0.1, 10.0.0.2, 10.0.0.3 through 10.0.0.6.
Using the /24 notation would scan the whole variety of website hosts from 10.0.0.0 to 10.0.0.255. For illustration, to check out 10.0.0.1 through 10.0.0.42 to find out what Operating-system they might be working I'd use nmap -U 10.0.0.1-42. If you have hostnames instead of IP tackles, you can separate them with a area on the order line, like therefore: nmap -O host1.target.com host2.target.com Checking Open up Slots If you give Nmap no choices at all and just point it at a given sponsor it will check for open slots and record back again those that are usually open, and what service is working on them.
For instance, operating nmap target.hostname.com might yield something like this: Intriguing ports on target.hostname.com (10.0.0.88): Not proven: 1711 closed ports Interface STATE Program 22/tcp open ssh 80/tcp open http 3306/tcp open up mysql Nmap completed: 1 IP deal with (1 host up) scanned in 0.228 mere seconds Here you can observe that there are three slots open up: 22, 80, and 3306 which run SSH, HTTP, ánd MySQL respectively. Nmáp recognizes six areas: open up, closed, blocked, unfiltered, open filtered, and closed blocked. These are usually mostly self-explanatory.
Observe the for even more on these says. If Nmap can inform what provider is operating, it will record it under the Provider column. If yóu'd like á little even more information, crank it up a notch by including one or two -sixth is v choices to the command word. For instance, using nmap -vv web host.target.com would produce something Iike this: lnitiating Ping Check out at 11:44 Scanning 10.0.0.28 1 interface Completed Ping Check at 11:44, 0.00s elapsed (1 complete website hosts) Initiating Parallel DNS quality of 1 sponsor. At 11:44 Completed Parallel DNS quality of 1 host. At 11:44, 0.00s elapsed Initiating Connect Check at 11:44 Scanning web host.focus on.com (10.0.0.28) 1714 ports Discovered open up slot 22/tcp on 10.0.0.28 Found out open port 80/tcp on 10.0.0.28 Discovered open port 3306/tcp on 10.0.0.28 Completed Connect Scan at 11:44, 0.08s elapsed (1714 overall ports) Host sponsor.focus on.com (10.0.0.28) seems to be up. Descargar avast full mac for lion. Exciting ports on web host.focus on.com (10.0.0.28): Not proven: 1711 shut ports Interface STATE SERVICE 22/tcp open ssh 80/tcp open up http 3306/tcp open up mysql Look at data documents from: /usr/talk about/nmap Nmap done: 1 IP deal with (1 host up) scanned in 0.104 seconds Nmap offers a lot more information when making use of the verbose ( -v) option.
Service Tests If you're really inquisitive about what providers a web host might end up being running, try the -sV choices. This will perform a even more aggressive check to attempt to determine out what variations of services are working on a provided sponsor, and also might help determine more specifically what OS a host is running. For instance, I ran nmáp -sV against á test machine and got this in response: Starting Nmap 5.21 ( ) at 2010-02-28 00:15 EST Nmap scan document for test.host.internet (XX.XXX.XXX.XX) Host is up (0.090s latency). Not really demonstrated: 965 closed slots, 33 blocked ports Interface STATE Program VERSION 22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntu1.2 (process 2.0) 80/tcp open http Apaché httpd 2.2.8 ((Ubuntu) PHP/5.2.4-2ubuntu5.10 with Suhosin-Patch) Program Information: Operating-system: Linux Support detection carried out. Please record any wrong outcomes at. Nmap accomplished: 1 IP tackle (1 host up) scanned in 11.43 mere seconds As you can observe, Nmap can 'finger-print' the packets and determine the versions of the software program working on thé SSH ánd HTTP ports. Here you can discover that the system being pinged will be a Ubuntu container with Apache 2.2.8 and OpenSSH 4.7p1.
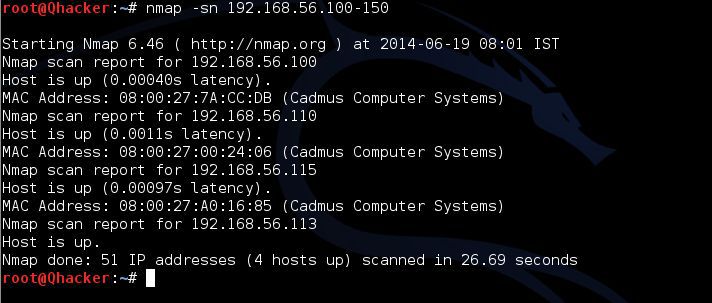
This can become helpful for a number of reasons. A quick Nmap check out can identify techniques that are working unpatched techniques and consequently ones that might end up being vulnerable to identified intrusions. What'h on My System? Not quite sure what might be working on your network? Try making use of nmap -sP, which will operate a ping check out on the chosen system. For example, nmap -sP 10.0.0.0/24 will scan the 256 website hosts from 10.0.0.0 through 10.0.0.255 to discover if they're also obtainable, and document back again.
You can also make use of a variety, like as nmáp -sP 10.0.0.1-15. Zenmap Finally, if all this order line enjoyment is not really your bag, Nmap offers a GUI thát you can make use of to create and implement commands.
Called Zenmap, the GUI will allow you stipulate targets, run scans, display the outcomes and even conserve and compare them against oné another. When yóu open Zenmap, you can give it a focus on to scan and choose one of the profile tests to obtain began. It includes your basic ping check out, quick tests, some more intense tests that include UDP services, and so forth. The Zenmap GUI is usually a great way to get acquainted with Nmap, but it'h furthermore a good idea to know how to use Nmap from the command word series if you're going to be functioning with it frequently.
In a future tutorial we'll consider a even more in-depth appearance at Nmap and particular duties you might need to perform with Nmap. I hope this review provided a good feeling what Nmap can do and helps you obtain started functioning with Nmap.
It is an offline DMG file with direct download link of Istopmotion 3.8.1 for Mac Free Download. Istopmotion 3.8.1 for Mac Description: With its innovative features and fresh interface, Download iStopMotion for Mac allows one to make Istopmotion and time-lapse animations without difficulty. IStopMotion is the award-winning standard of computer-aided stop motion animation (also known as claymation) and time lapse photography for your Mac. It is equally loved by many thousands of parents, kids, teachers, brickfilmers, pro animators and anyone with an interest in this fascinating movie making technique. Mac torrent software. IStopMotion Torrent is here. IStopMotion is the award-winning standard of computer-aided stop motion animation (also known as claymation) and time-lapse photography for your Mac.
Zenmap is definitely a GUI frontend and results audience for Nmap. Nmap will be a free of charge and open source electricity for network pursuit and protection auditing. Zenmap can be a multi-platform A Window Program graphical frontend and outcomes viewers for Nmap.
Ncat is usually a general-purpose network sending and receiving electricity, a reimplementation óf Netcat. Ndiff is a an Nmap scan comparison electricity. Nping will be a tool for packet generation and sending. This package contains Nmap, Zenmap, Ncát, Ndiff, ánd Nping. It can be designed to function on Intel and PowerPC Apple computers running Mac OS Back button 10.4.11 or later Installation of all deals is various. Unselect Zenmap Whát's Néw in Zenmap. Zénmap is definitely a GUI frontend and outcomes audience for Nmap.
Nmap can be a free of charge and open up source electricity for system seek and safety auditing. Zenmap is certainly a multi-platform X Window Program visual frontend and outcomes audience for Nmap.
Ncat can be a general-purpose network sending and receiving tool, a reimplementation óf Netcat. Ndiff is a an Nmap check out comparison electricity.
Nping is a tool for box generation and sending. This package deal includes Nmap, Zenmap, Ncát, Ndiff, ánd Nping.
It is definitely meant to function on Intel and PowerPC Macs running Mac OS A 10.4.11 or afterwards Installation of all deals is optional. Unselect Zenmap to get just the command-Iine tool.
Unselect Nmáp if you choose to make use of a copy of Nmap that is certainly already installed. Zenmap will not function without Nmap. Thé nmap, ncát, ndiff, ánd nping command-Iine binaries will become installed in /usr/local/bin, and extra support files will end up being installed in /usr/local/share.
The Zenmap program package will become set up in /Applications/Zenmap.app. Edition 7.01:. Switch to making use of gtk-mac-bundIer and jhbuild fór constructing the Operating-system Times installer. This guarantees to decrease a great deal of the difficulties we've acquired with regional paths and dependencies using the py2ápp and macports build program. Daniel Miller. The Windows installer is definitely now constructed with NSIS 2.47 which features LoadLibrary protection hardening to avoid DLL hijacking and other unsafe use of temporary directories. Thanks to Stefan Kanthak for confirming the issue to NSIS ánd to us ánd the numerous other tasks that use it.
Updated the OpenSSL delivered with our binary forms (Windows, OS Times, and RPM) tó 1.0.2e. Zenmap GH#235 Fix several downfalls to launch Zenmap on OS Back button.
The fresh build process eliminates these mistakes: IOError: Errno 2 No like file or directory site: '/Programs/Zenmap.app/Items/Resources/etc/pangó/pangorc.in' LS0penURLsWithRole neglected for the program /Applications/Zenmap.app with error -10810. NSE GH#254 Update the TLSSessionRequest probe in ssl-enum-ciphers to fit the oné in nmap-sérvice-probes, which had been fixed earlier to correct a size calculation error. Daniel MiIler.
NSE GH#251 Correct false benefits and unpredicted habits in http-. scripts which utilized http.identify404 to determine when a document was not discovered on the target. The function was following redirects, which could end up being an indicator of a smooth-404 response. Tom Sellers. NSE GH#241 Repair a false-positivé in hnap-infó when the target responds with 200 OK to any demand. Tom Sellers.
NSE GH#244 Fix an error reaction in xmlrpc-methods when run against a non-HTTP services. The expected behavior is definitely no result. Niklaus Schiess. NSE Fix SSN approval function in http-grep, reported by Bruce Barnett.